Compliance-focused cyber assessments ensure that a system meets the letter of the law and the list of policy requirements by following the National Institute of Standards and Technology Risk Management Framework and/or Cybersecurity Framework. Authority to Operate is often the definition of success for these assessments but is not a guarantee of security. Attackers do not care if you are compliant!
Mission-focused cyber assessments should provide decisionmakers with prioritized, actionable ways to reduce cyber risk (i.e., mitigate vulnerabilities). A cybersecurity assessment should be a tailored evaluation based on the context of the mission, organization, architecture, and systems to determine the critical assets. Security techniques are then applied to mitigate threats and vulnerabilities to acceptable levels of risk. Cyber assessments must evaluate mission assets at each level, layer, and subsystem in addition to analyzing the architecture as an integrated whole.
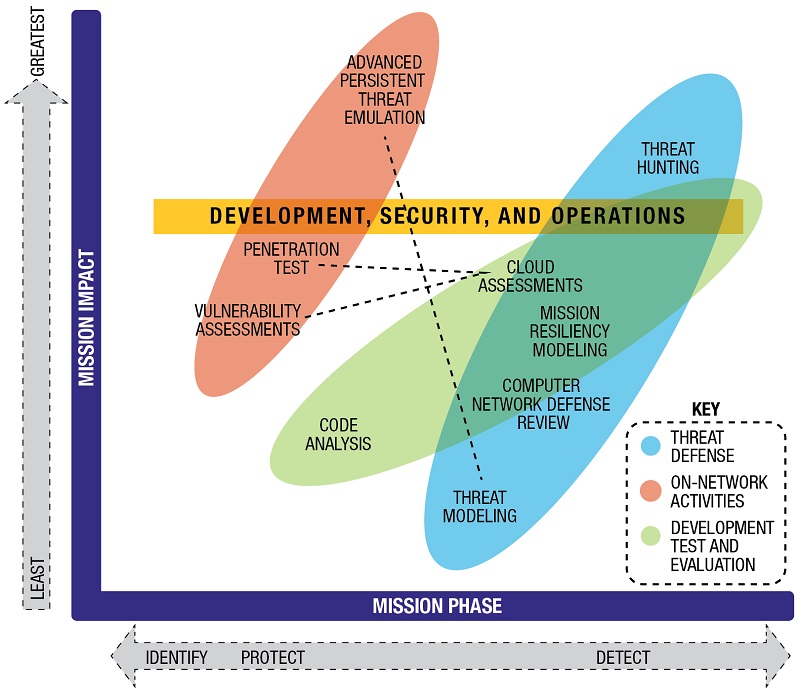
Modeling the “mission thread” provides the opportunity to identify the critical assets to further assess potential points of vulnerability. The mission’s adequacy can be evaluated across all phases of operations and layers throughout the architecture.
In practice, this involves working with many technologies and corresponding techniques for managing threats on critical assets such as:
- Supporting infrastructure: layer-2 and layer-3 network devices, controlled interfaces and firewalls, cybersecurity defense mechanisms, threat hunting
- Industrial control systems, operational technology
- Software: security evaluation, static, binary, and dynamic code analysis
- Mission-critical assets: identity and access management, command and control, data processing
Cyber assessments too often focus solely on compliance, rather than testing for effective security practices.
Assessment methods should evaluate mission impacts across all mission phases through mission risk-focused testing to determine the cyber-based technical ground truth.
For more information, contact Thomas Axberg or Robert Heald.
This story appears in the June 2020 issue of Getting It Right, Collaborating for Mission Success.