Software intended for operational ground systems must be tested to ensure that it meets technical requirements and doesn’t introduce security vulnerabilities. Often, the software assurance process is not as robust as it could be.
As part of this process, developers will analyze the code against a list of common weaknesses1 to demonstrate immunity. A single static analyzer is often used for this step. While various analyzers can check a few hundred of the 714 common weaknesses, no single tool catches more than about half of the 50 most critical weaknesses for a satellite ground station.
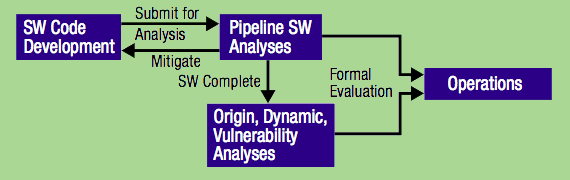
In light of this, Aerospace built an automated web-based tool that creates a pipeline capable of executing several software analyzers that collectively catch from 90% to 99% of those critical weaknesses (depending on the coding language). Results from each analyzer are available to developers, and a combined report is prepared for the authorizing officer to support rapid transition to operations.2
While automated analysis of software is not new, combining the tools that best catch this level of critical weakness for satellite ground stations is a step forward. Using it in a rapid development environment will expedite the release of software to the operational site.
1 Common Weakness Enumeration, https://cwe.mitre.org.
2 Software Assurance Pipeline Recommendations for the Space Defense Task Force, Aerospace Report No. TOR-2018-01105, The Aerospace Corporation, El Segundo, CA (April 30, 2018). Restricted distribution.
This story appeared in the December 2018 issue of Getting It Right, Collaborating for Mission Success.
Subscribe to Getting It Right


